Protecting Your Identity, Data and Assets

It’s Not a Matter of If, but When…

Common Cyber Threats
- Email Account Takeover
- Malware
- Phishing
- Credential Replay
- Social Engineering
- Call Forwarding
- Spoofing
Email Account Takeover
What is it?
A cybercriminal hacks an email account and reads emails to learn about the victim and their habits so they can pose as the victim to steal money.
What does it look like?
Your email is hacked, and posing as you, the cybercriminal emails your advisor instructions to forward funds to an account.
How does it happen?
Cybercriminals find vulnerabilities within service providers’ servers or personal users’ IP addresses to gain access to login credentials, or to the email account directly.
What’s the impact?
Because the cybercriminal has access to your email and can impersonate you, the recipient of the cybercriminal’s email believes the correspondence comes from you. The cybercriminal may provide instructions within the email to transfer funds to a fraudulent account. Without proper verification, the money could be transferred and stolen.
How can you defend against it?
Follow proper identification processes. Use secret passwords, phone call verifications, and video chats to help verify the identity of people you correspond with.
Malware
How does it work?
Malicious software is created to damage/disable computers and computer systems, steal data, or gain unauthorized access to networks.
What does it look like?
Examples of malware include viruses, worms, trojan horses, ransomware, and spyware.
How does it happen?
Malware may be installed on a computer when a user clicks an unsafe link, opens an infected file, or visits a legitimate website that could contain adware.
What’s the impact?
Malware can delete files or directory information, or it may allow attackers to covertly gather personal data, including financial information and usernames and passwords.
How can you defend against it?
Install the most up-to-date antivirus and anti-spyware software on all devices that connect to the Internet and run regular scans to update the software when available.
Make sure your networking equipment and computers are all still supported by the manufacturer.
Phishing
What is it?
Cybercriminals pretend to be a trustworthy source in order to acquire sensitive personal information such as usernames, passwords, social security numbers, and credit card details.
What does it look like?
An email from a seemingly legitimate email address instructs you to click on a link to take action (e.g., “validate your account,” “confirm your identity,” “access your tax refund”). The link brings you to a website requiring you to enter your personal information.
How does it happen?
Because the cybercriminal masquerades as a legitimate source (e.g., financial institution employee, realtor, banker), you believe the request is from a trusted source and you unwittingly oblige when they ask you for your personal information.
What’s the impact?
Victims of phishing may have malware installed on their computer systems or have their identity stolen.
How can you defend against it?
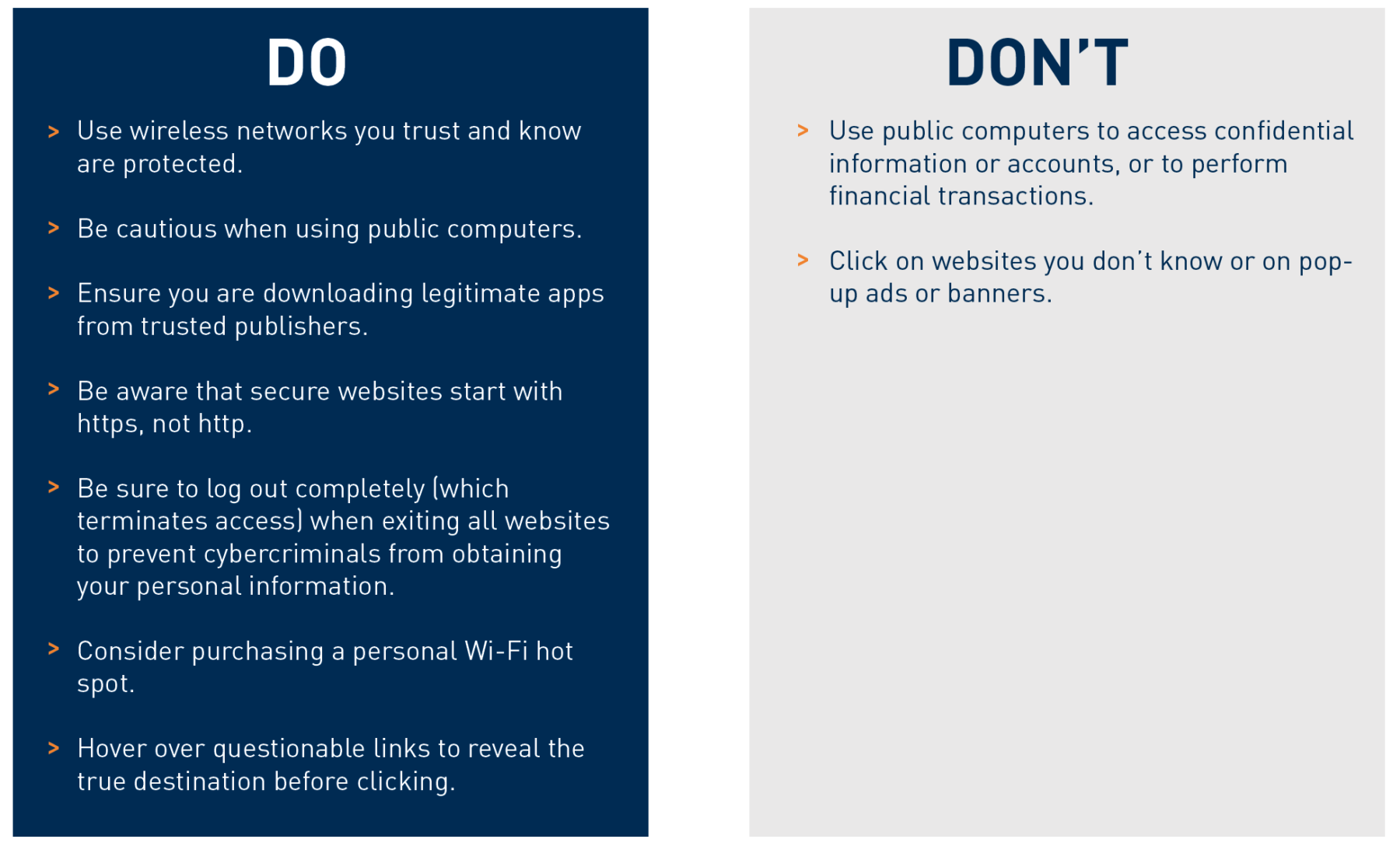
Hover over questionable links to reveal the true destination before clicking.
Beware that secure websites start with https, not http.

Credential Replay
What is it?
Most people re-use passwords and usernames. Cybercriminals obtain these login credentials, test them in large numbers against financial institutions’ websites to find matches, and then request fraudulent fund transfers.
What does it look like?
Cybercriminals hope to access a few accounts by using a large cache of stolen login credentials to access a firm’s online accounts.
How does it happen?
Cybercriminals can easily purchase large numbers of stolen login credentials from the dark web.
What’s the impact?
Your account is compromised, and the cybercriminal can quickly re-use your credentials to access other accounts, and steal additional funds and your confidential data before detection.
How can you defend against it?
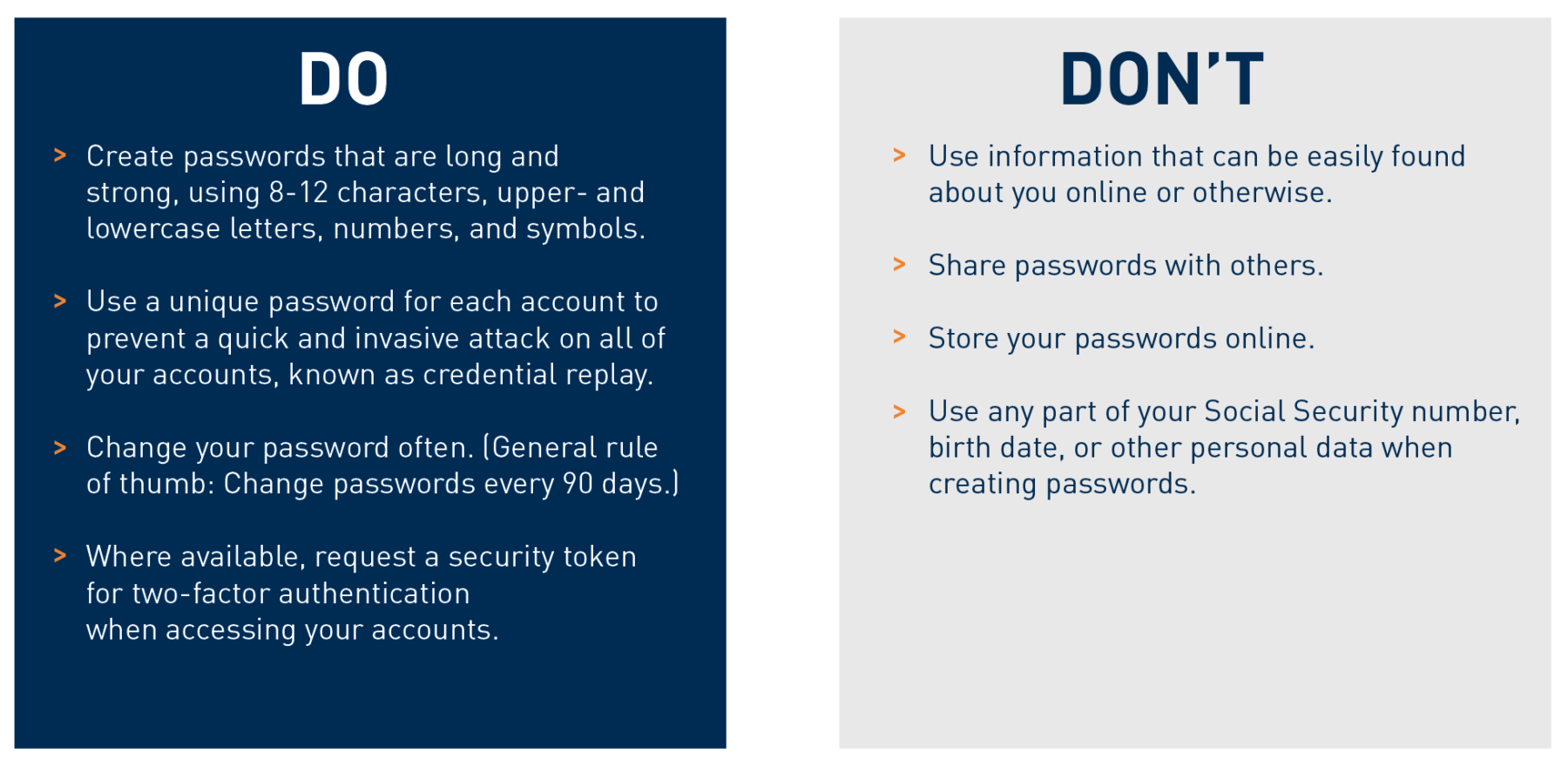
Use a unique password for each account to prevent a quick and invasive attack on all of your accounts.
Make each password unique and long and strong. Use 8-12 characters, upper- and lowercase letters, and symbols.
Social Engineering
What is it?
This involves manipulating or impersonating others to divulge sensitive, private information, and then demanding financial transactions be executed to avoid consequences.
What’s the impact?
The cybercriminal commits fraud, steals your money, and disappears.
How can you defend against it?
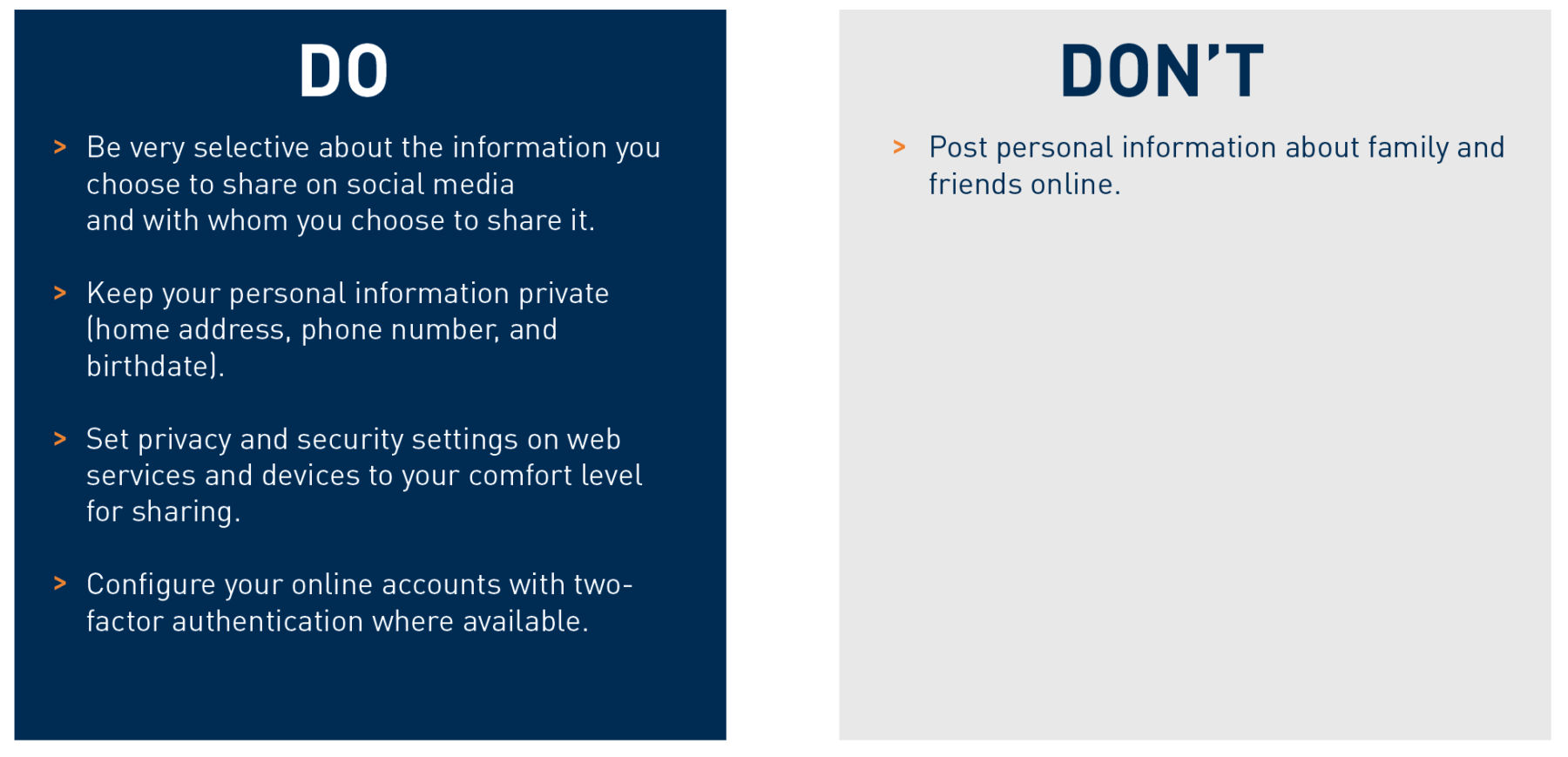
Be selective about who you allow to join your social networks.
Be cautious about the information you choose to share on social media, keeping your personal information private (e.g., home address, phone number, employer, vacation dates, birthdate).
Call Forwarding
What is it?
The cybercriminal takes over your cell phone number and impersonates you or reroutes your calls.
What does it look like?
A cybercriminal gets the phone company to forward your cell number to their cell phone so they can impersonate you when your bank calls you back for verification before transferring funds or opening accounts.
How does it happen?
Cybercriminals scam the phone company into forwarding phone calls. They may also use scanners, eavesdrop, clone your phone identity, and sell bogus ringtones or other gadgets to access your phone.
What’s the impact?
Your phone is compromised, your conversations may be accessed, and your identity may be stolen.
How can you defend against it?
Follow proper identification verification processes. Consider using secret passwords to help verify the identity of people you’re corresponding with.
Check your monthly phone bill for any suspicious activity. This may include phone numbers you don’t recognize or calls placed at odd times (e.g., during works hours, while overseas or on vacation).
Spoofing
What is it?
A fake email header that gives the impression the email is from someone or somewhere other than the actual source, with the goal of tricking the recipient into opening and responding to the email. Phone spoofing is a comparable common cyber threat using a similar phone number.
What does it look like?
Your advisor receives an email from a cybercriminal who impersonates you and confirms a fraudulent wire transfer request.
How does it happen?
The cybercriminal creates an email address nearly identical to your email address (i.e., off by a character).
What’s the impact?
Similar to the other cyberattacks we’ve discussed, your money is stolen, and you become the victim of fraud and/or identity theft.
How can you defend against it?
Carefully check the incoming emails for the proper email address and the accuracy of the spelling of the sender’s name.
If an email or phone call are questionable, contact the sender directly, using the email address or phone number you have on file for that individual.
How Cybercriminals Use Stolen Data
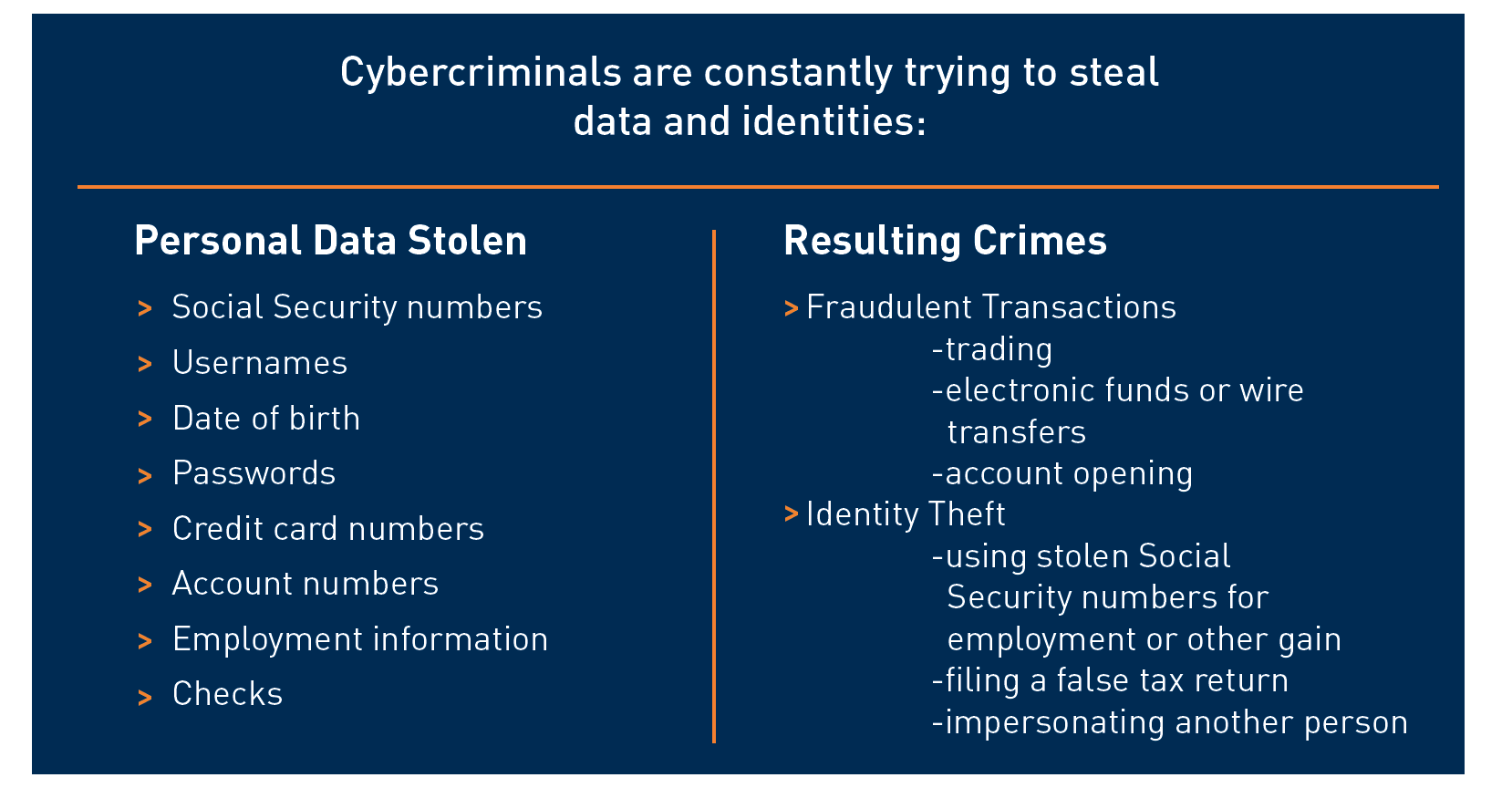
Identity Theft is Everyone’s Problem

How We Protect Your Data
Cybersecurity Program
Acumen strives to stay on top of the latest news to keep your information secure. We invest heavily in IT resources and conduct testing to ensure it is working properly.
Staff and Vendor Vetting
Acumen conducts background checks on employees and checks vendor information to ensure they are doing all they can to keep information secure. We have vendors sign non-disclosure forms and work to conduct onsite due diligence when possible.
Staff and Vendor Training
Acumen partners with Advisor Armor who provides employees with quarterly training and phishing tests to keep us all aware. We require all vendors to notify us of any breaches that occur within their systems.
Ongoing Client Education
Acumen works to keep clients updated on the latest trends in cybersecurity by providing information such as this piece to help clients be aware. We can be followed on LinkedIn and Facebook for more information.
Authentications and Funds Transfer Policies
Acumen will not accept electronic instructions to transfer money into or out of your account. We will work to verbally confirm all money movement instructions. Passwords can be added to your account at your discretion.
How You Can Protect Your Data
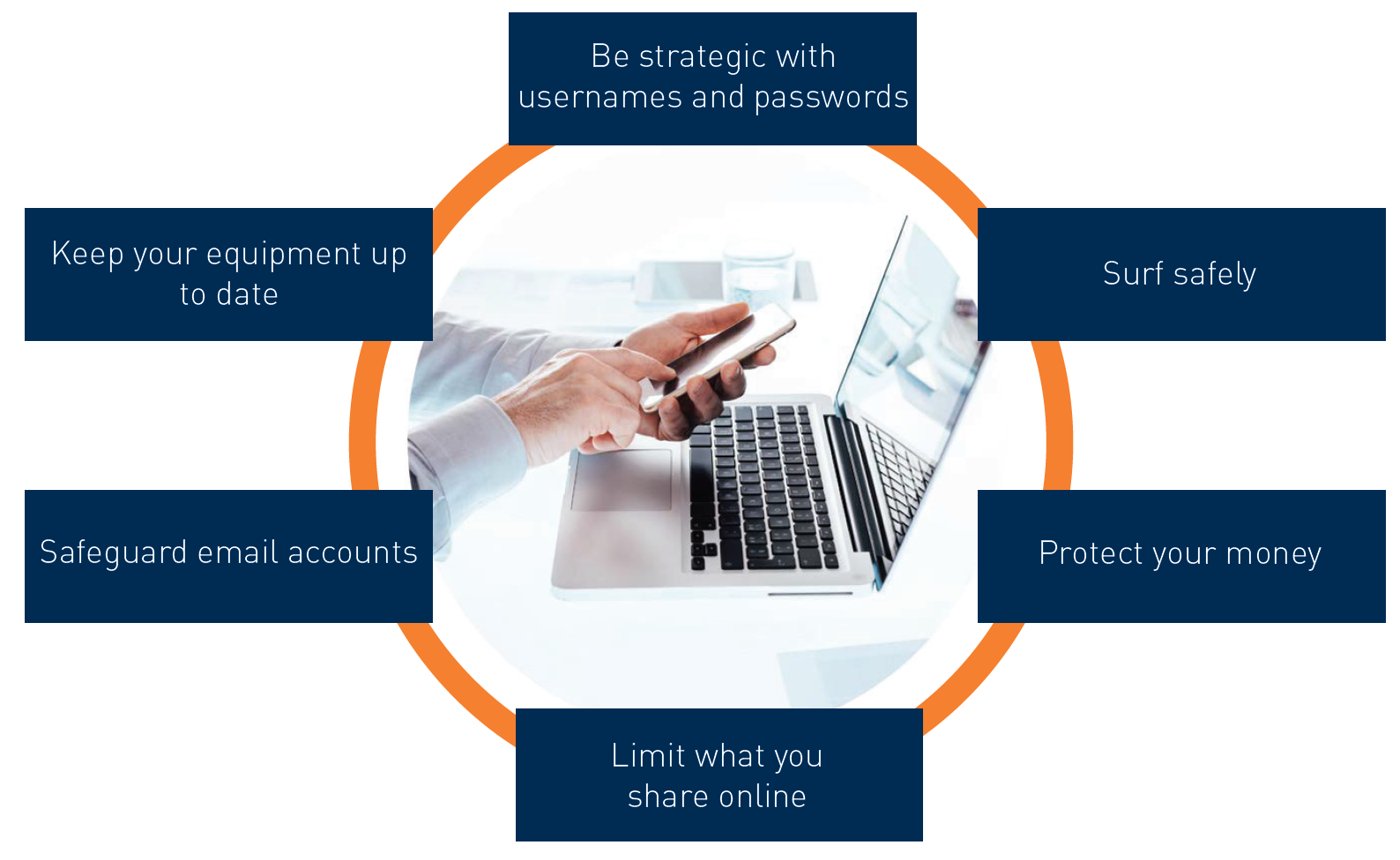
Be Strategic with Usernames/Passwords
Surf Safely
Protect Your Money

Limit What You Share Online
Safeguard Your Email Accounts

Keep Equipment Up to Date

Resources
Acumen Wealth Advisors
423-825-496
clientservices@acumenwealth.com
Charles Schwab & Co., Inc. Resources:
Schwab Alliance at 1-800-515-2157 to validate suspicious emails
Visit Charles Schwab Client Learning Center
Additional Resources:
TransUnion | 1-800-680-7289 | https://www.transunion.com/
Experian | 1-888-397-3742 | https://www.experian.com/
Equifax | 1-888-766-0008 | https://www.equifax.com/

Acumen Wealth Advisors, LLC® is a Registered Investment Adviser. Advisory services are only offered to clients or prospective clients where Acumen Wealth Advisors, LLC® and its representatives are properly licensed or exempt from licensure. Past performance is no guarantee of future returns. Investing involves risk and possible loss of principal capital. No advice may be rendered by Acumen Wealth Advisors, LLC® unless a client service agreement is in place.